Third Party Risk Protection
Ensure you are putting your trust in the right areas
Assure that those you trust are trustworthy
Those with access to your networks
One of the greatest risks are vendors, contractors and other third parties with access to your network. Using techniques such as spear-phishing, miscreants acquire valid credentials to gain access to your network. Once inside your network, they broaden their footprint by moving across VLANs. Attack via VPN can leave your network infrastructure at risk as threat actors can scan for vulnerable open ports and unsecured devices.
Those holding your data
Another major area of potential vulnerability are third parties processing your sensitive data or rather how well are they guarding your data. Keeping your data on servers visible on the internet substantially increases your vulnerability even if the data stored is encrypted.
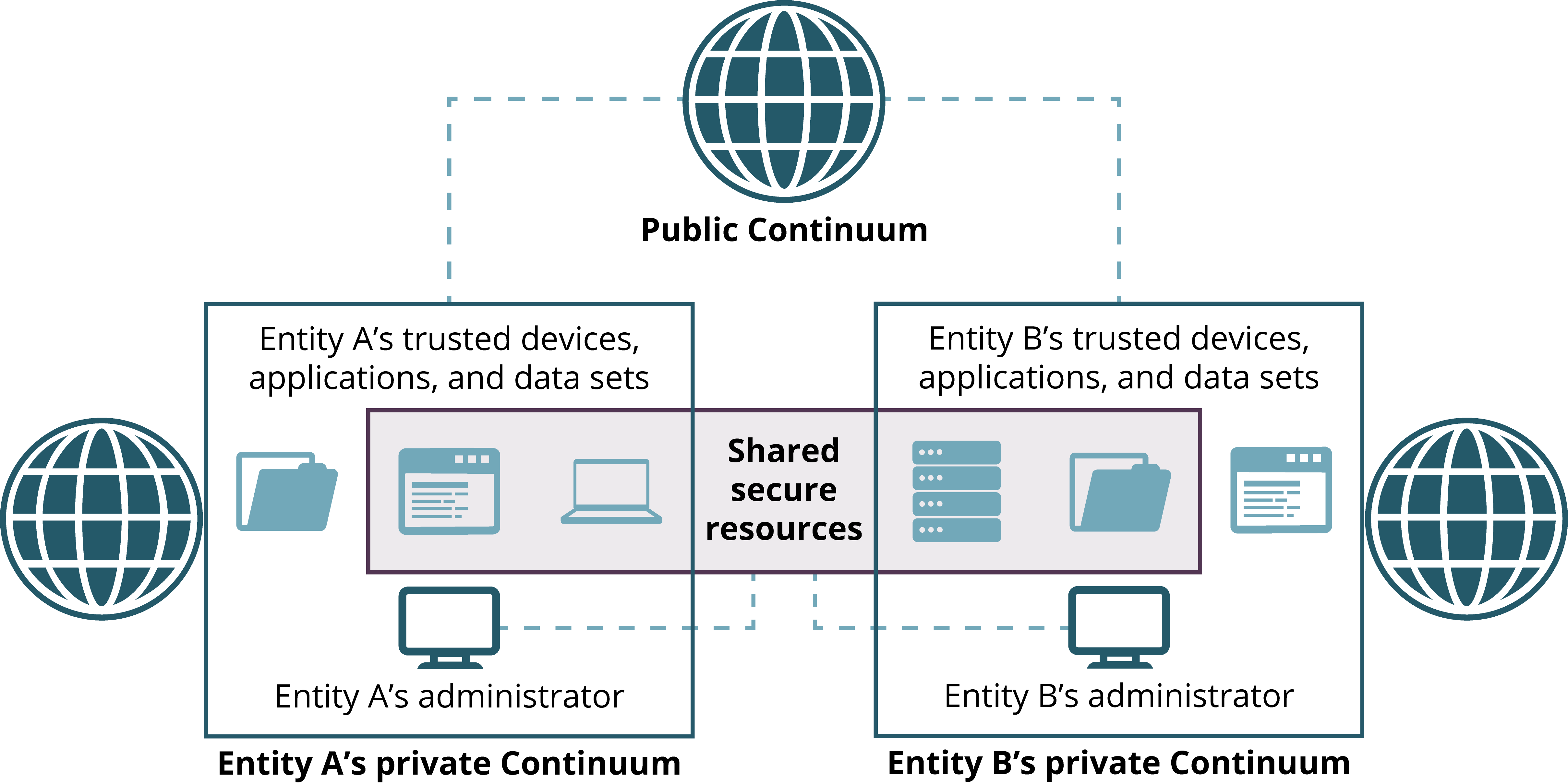
The data you’re holding for others
Failing to protect your customers’, partners’ and vendors’ data can lead to severe implications such as financial liability, legal damages and most importantly loss of reputation of your business. With the ever-evolving perimeter today, traditional remote access VPN technologies need to make way for more scalable and isolated third party access capabilities.
Our routing network works on the basic tenet that something that is not visible cannot be hacked. It accomplishes this by hiding servers housing third party data behind all-inbound blocked firewalls. This makes the servers invisible on the internet, only receiving request from authenticated sources.
Limiting third party risk from unauthorized access
Relying on user names and passwords is ineffective in today’s sophisticated threat environment. And today’s security solutions, even when used in depth, aren’t capable of mitigating risks associated with third-party access. SAIFE has created a user-centric context-aware model that defines access by the user, their device, and where they are located that renders stolen credentials useless. Access is established to only those data or applications that they are entitled to access. SAIFE ensures that all endpoints attempting to access a given infrastructure are authenticated and authorized prior to accessing any resources on the network; unauthorized network resource are inaccessible. SAIFE effectively creates a dynamic, individualized perimeter for each user based on attributes such as identity, device profile, location, and authentication method.

